Colorado Medical Society
http://dev.cms.org/articles/cyber-alert-how-to-protect-your-practice-from-hackers/Cyber alert: How to protect your practice from hackers
Tuesday, May 16, 2017 12:25 PMThe United States Computer Emergency Readiness Team (US-CERT) has received multiple reports of ‘WannaCry’ (also known as ‘WannaCrypt’) ransomware infections in several countries around the world and in the United States. Some of these infections are impacting patient access to care. Ransomware is a type of malicious software that infects a computer and restricts users’ access to it until a ransom is paid to unlock it. Individuals and organizations are discouraged from paying the ransom, as this does not guarantee access will be restored.
In addition to the information provided below, the American Medical Association (AMA) has resources to help physicians conduct a checkup of their systems, and to secure their networks and office computers. Additionally, the AMA has been engaged with the administration since the cyberattack and will continue to monitor the situation. Please let us know by replying to this email whether you have been impacted by the WannaCry infection.
What should I do now?
Ransomware can infect computers and medical devices. The WannaCry infection affects systems running Windows and spreads easily when it encounters unpatched or outdated software. Physicians should ensure that their computer’s operating systems and anti-virus software are updated and patched:
- Run Windows Update immediately. Download and install any available updates (‘patches’). Run a scan on your anti-virus software and follow its prompts. Microsoft has released a customized patch for older platforms that do not receive mainstream updates, including Windows XP, Windows 8, and Windows Server 2003. At this time, Windows 10 has not been targeted by the attack.
- Check your computer’s settings to ensure that the system will automatically download and install new versions of the operating system and Microsoft Office software. Do the same for your anti-virus software.
- Note when the computer will install these new updates and make sure the computer is on at that time.
In addition, physicians should contact their medical device vendors and manufacturers to ensure that they have patched their device software. Medical device manufacturers can always update a medical device for cybersecurity; the FDA does not typically need to review changes made to medical devices solely to strengthen cybersecurity.
How to help protect yourself from downloads and email-based ransomware
Ransomware can be delivered via email by attachments or links within the email. Attachments in emails can include documents, zip files, and executable applications. Malicious links in emails can link directly to a malicious website the attacker uses to place malware on a system. To help protect yourself, be aware of the following:
- Only open emails from people you know and that you are expecting. The attacker can impersonate the sender, or the computer belonging to someone you know may be infected without his or her knowledge.
- Do not open email attachments from an unknown, suspicious, or untrustworthy source. If you’re not familiar with the sender, do not open, download, or execute any files or email attachments.
- Do not open an email attachment unless you know what it is, even if it appears to come from a friend or someone you know. Some viruses replicate themselves and spread via email. Stay on the safe side and confirm that the attachment was sent from a trusted source before you open it.
- Do not open any email attachments if the subject line is questionable. If you think that the attachment may be important to you, always save the file to your hard drive before you open it.
- Vigilance is the best defense against phishing scams. “Phishing” describes email scams that attempt to acquire confidential information such as credit card numbers, personal identity data, and passwords. Often these emails look like they come from real companies or trusted individuals. If you want to find out whether the email is legitimate, contact the company via their published customer service contacts. Do not reply to the email or click on any links.
- Exercise caution when downloading files from the internet. Make sure that the website is legitimate and reputable. If you have any doubts, don’t download the file.
- Do not open messages or click on links from unknown users in your instant messaging program. Instant messaging can be a vehicle for transmitting viruses and other malicious code, and it’s another means of initiating phishing scams.
Example of Ransomware
This is an example of what the ransomware may look like:
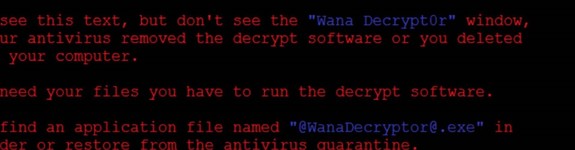 ted
ted
What to do if you have been infected
If your organization is the victim of a ransomware attack, contact law enforcement immediately.
- Contact your FBI Field Office Cyber Task Force immediately to report a ransomware event and request assistance. These professionals work with state and local law enforcement and other federal and international partners to pursue cyber criminals globally and to assist victims of cyber-crime.
- Report cyber incidents to the US-CERT and FBI’s Internet Crime Complaint Center.
- For further analysis and health-care-specific indicator sharing, please also share these indicators with HHS’ Healthcare Cybersecurity and Communications Integration Center (HCCIC) at HCCIC_RM@hhs.gov.
Additional resources
- The U.S. Computer Emergency Readiness Team – US-CERT.gov
- HHS Office of Civil Rights Guidance on HIPAA and Ransomware
- The FDA’s Role in Medical Device Cybersecurity
- HHS ASPR - Technical Resources, Assistance Center, and Information Exchange (TRACIE) Healthcare Emergency Preparedness Information Gateway’s cybersecurity resources
- The Office of the National Coordinator for Health Information Technology’s (ONC) SAFER Guides, which include ransomware prevention and mitigation strategies (for more information, see the AMA’s recent Advocacy Update)